The Information Security Roadmap
Finally, as the commencement of information security work is nearing, almost invariably this question is being asked:
What are the steps to improve our security posture?
We offer an Information Security Roadmap to answer this question.
This roadmap is integrated with the Information Security Management, and with the Implementation Frameworks. In our experience the individual pieces of the incorporated entity's information security posture are better understood through a coherent, manageable plan. Part of the learning process is to understand what needs to be implemented immediately and what can be done later.
This does not mean that the roadmap replaces any of the above frameworks. Rather, it provides another view of those frameworks, listing necessary components and processes together, showing their dependencies and interrelations. As with the implementation framework, we consider the roadmap to be cyclical in nature. As the informations security maturity and capabilities of the incorporated entity grow, components can be revisited, improved or made more complete.
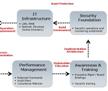
The diagram below depicts a segment of such Information Security Roadmap:
Please click on the image for a larger version.
The use of such roadmap is beneficial, because it is
- Based on the other frameworks we offer
- Cyclical, therefore improvements can be accumulated
- An end-to-end solution with
- A risk based approach.
For relevant capabilities please read the Technology Implementation section in the Management category here, and the Security Training section in the Consulting category here.
If we can assist you in any ways please feel free to contact us for further information. Our consultants will be happy to assist you with your enquiry.