Information Security Literature Grouping
The landscape of (information security) governance literature is rather complex. The subtle differences – between seemingly similar views – would be difficult to understand without categorising them. In order to facilitate better understanding, different views are illustrated by the following diagrams in Figure 1 and Figure 2.
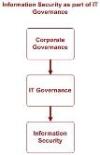
Figure 1
Please click on the image for a larger version.
The structure depicts a hierarchy of components in the area to be studied. Corporate governance literature, which sits at the highest level, obviously contains more areas than IT governance or information security. Areas like management accounting, ethics, corporate law etc. are also part of corporate governance and will be reviewed to varying degrees. However, in order to see where information security governance fits into this system, this high-level diagram can be sufficient.
An important aspect of this diagram is the hierarchical structure that seems to exist from corporate governance to information security management, each one being a subset of the one above. The hierarchy also represents a thought, that moving down on the hierarchy; the disciplines become more technology oriented. The result of this thinking is a view that that information security is solely a technological issue. Consequently information security is a barrier to commerce (Control Data, 1999).
Even when information security is not viewed as a technological issue, it is still considered as a subset of IT governance (ITGI 2, 2001). While it is a major improvement on the “technological issue only” view, significant limitations remain inherent in this view. Information security is still considered a value preserver only (ITGI 4, 2003).
A word of caution is appropriate here though. While this view is widely accepted, no empirical study seems to exist to support it. Assertive statements from the ITGI (ITGI 2, 2001) are not backed by solid theory development, and therefore the validity of such a view is at least questionable. This does not mean the view is incorrect or faulty. It simply means that a gap seems to exist in literature, and further research should be carried out to cover this gap.
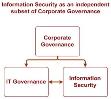
The other major structure as shown in Figure 2 treats information security governance at an equal level with IT governance.
Figure 2
Please click on the image for a larger version.
Literature that can be described by this diagram considers that information security is a business issue (The Vantage Group), rather than a technological issue. Companies that take this approach treat information security decisions as strategic in nature. In such companies information security is an independent subset of Corporate Governance. Strong interrelations exist between IT in general and information security though, as security engineering practices are built into the entire life cycle of systems (SSE-CMM).
The importance of these two approaches is immediately recognisable in the operational and organisational structure of an enterprise. The former view lists information security among the responsibilities of the Chief Information Officer (CIO) (Deloitte TT, 2004, p. 17). The second view assigns information security to the Chief Information Security Officer (CISO) or Chief Security Officer (CSO), who reports to a senior business executive (Hunt, 2004).
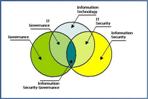
The areas of corporate governance, IT governance and information security governance often overlap. The Venn diagram in Figure 3 (courtesy of Jason Taule, at Jason-T@vips.com , mailed to the IT Governance listserv, used here by permission) presents one view of such overlap. The importance and benefit of understanding such overlaps can be realised in refined organisational structure and roles and responsibilities.
Figure 3
Please click on the image for a larger version.
The organisational structure and assigned responsibility are important factors in determining the role information security has in the organisation’s life. It is worthwhile to investigate further how these factors influence the value creating abilities of information security governance. It is theorised, that the overlaps are similar in nature and the rules along the overlaps are identical or closely identical at each level. However further studies are required to build such theories and empirically test them.
References
- Control Data Systems, Inc., 1999, Why Security Policies Fail, viewed 17 May, 2004, http://downloads.securityfocus.com/library/Why_Security_Policies_Fail.pdf
- Deloitte TT, 2004, 2004 Global Security Survey, Deloitte Touche Tohmatsu, viewed 12 Nov 2004, http://www.deloitte.com/dtt/cda/doc/content/dtt_financialservices_SecuritySurvey2004_051704.pdf
- Hunt,S. 2004, “The CISO in 2010 still touches technology”, in CSO Magazine viewed 20 May, 2004, http://www.csoonline.com/analyst/report2566.html
- ITGI 2 (IT Governance Institute), 2001, Information Security Governance: Guidance for Board of Directors and Executive Management, IT Governance Institute (ITGI), viewed 17 May 2005, www.itgi.org
- ITGI 4 (IT Governance Institute), 2003, IT Governance Executive Summary, viewed 18 April 2004, www.itgi.org
- SSE-CMM Project Team, 1999, Systems Security Engineering Capability Maturity Model, SSE-CMM Model Description Document Version 2.0, viewed in early 2003, http://www.sse-cmm.org
- The Vantage Group, Security Policy Development, viewed 5 May, 2004, http://www.vantage-grp.com/Broch%20PDF/1a_Security%20Policy2.pdf