Information Security Policy, Standards, Procedures, etc.
There are mainly two schools of thought about the hierarchy of information security policies, standards, procedures, etc. These schools of thoughts can be separated by how the policies/standards relationship is viewed.
One school views Standards at the top of the hiearchy. This view emphasises that while company information security policies can change as the requirements change, the technology remains relatively constant. Consequently the appropriate policies are subject to these overarching standards.
The other school of thought places policy above standards. This view considers that the organisation's requirements drive what technology is going to be used. Therefore standards are subject to the requirements expressed in the policies. There are certain differences even within this view. Some consider many policies, or even multiple levels of policies. Standards can be even more granulated. The resulting policy/standard hierarchy is very complex, and often complicated. Others consider a single, overarching policy. I discuss this view in details as follows:
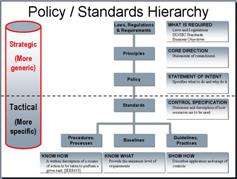
This picture visualises the framework being discussed.
Please click on the image for a larger version.
External variables such as laws and regulations influence the formation of organisational requirements. These are stated in the organisational objectives, and the information security policy makes the necessary alignments and sets the core directions for information security. The information security standards then describe how available resources shall be used to meet the policy requirements, thus creating specifications for controls. Baselines provide a minimum set of requirements, providing further details about the required controls. Procedures and practices explain detailed steps or actions to be taken in order to achieve those requirements. Guidelines and processes show the usage of controls and how the intent expressed in the policy can be achieved. While this description is somewhat simplistic, this hierarchy is workable and provides an easy enough framework that establishes the organisation’s security posture.
One important aspect of this hierarchy is how the framework changes from strategic to tactical. The policy document is usually concise. Descriptions are usually generic and set the high level parameters. The standards are usually more specific, as both the "whats" and "hows" are discussed. The details down to minute level are described in the procedures, guidelines, baselines, etc.
This change from strategic to tactical is also noticeable by the language used. Policies and Standards contain more formal statements. Words like "shall", "must", etc. dominate in Policies and Standards. Procedures and other tactical documents use words like "should", would", "can", etc.
Another benefit of this approach is its ability to easily conform to ISO/OEC 17799:2005 and ISO/IEC 27001:2005 at every level, while specific local requirements can still be observed. This built in conformity and flexibility is achieved by using modular development approach from standard level downward.
The framework provides a consistent approach from governance to operation. The audience at different levels of the hiearchy differs greatly, and the development of the hierarchy needs to carefully consider it. However the use of such hiearchy is rather beneficial as it provides a complete framework for any particular area or audience.