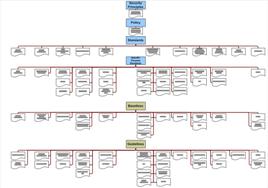
Information Security Policy Framework
The information security policy hierarchy discussed on the previous page can be implemented as a policy/standard framework. I note here that this framework needs to be carefully considered, because that can form the backbone of the organisation's information security management system (ISMS). I usually build such an ISMS around a core set of the policy/standard framework discussed here, including at least the principle statements and the policy document. Ideally I prefer to have a few standards as well, but life often dictates otherwise. Since the principle statement provide the core direction and the policy is the statement of intent, I do not see any ways to start without them.
The full framework is shown in the diagram below. The following discussion attempts to explain the diagram and the thinking behind this framework, highlighting some essential elements.
Please click on the image for a larger version.
Principle and Policy Statements
The principle statements should be expressed in a succint, high level document. These statements can provide the authoritative directives at each level of the policy hierarchy and can also serve as legal reference points. I found it essential to limit the number of statements, preferably not having more than a dozen to maintain clarity and a relatively high level. I usually include a definition of information security in this document, that sets the boundaries of the ISMS.
The policy document provides a central point of reference to each document in the hiararchy below, whether it is a standard, baseline or guideline. The policy follows the ISO/IEC 17799:2005 structure. The one notable difference to the ISO standard is that the first domain is extended in this document. The security policy is viewed as part of the information security governance framework. It is appropriate to make statements of intent about this wider framework rather than keeping a narrower focus of policy only.
I make every effort to keep the statements short and as clear and unambiguous as possible. The aim is to have one possible interpretation only. As this document is the central point of reference such clarity is mandatory.
Domain and Specific Purpose Standards
As I move one level down, I expand the structure, and have a standard document for each of the eleven ISO/IEC 17799:2005 domains. I call these standards "domain standards". These standards develop further what is contained within the policy, yet keep the ISO/IEC 17799:2005 structure. The standard format at this level includes:
- the standard statement
- reference to upper level documents
- list of risks addressed
- comments
The next layer consist many documents I call "purpose specific standard". These standards follow the ISO/IEC 17799:2005 structure as well. For example one can find standards under the domain "Access Control" discussing 3rd party access, remote access, etc. The "Communications And Operations Management" domain would have Antivirus, Firewall, etc. standards. The format of these documents differs from the domain standards, and even from each other, but the main components include:
- the standard statement
- brief justification for the standard statement
- short comments on the intent and best practice
- key performance indicators
- tips and warnings
- reference to related documents
Baselines, Guidelines, etc.
The next levels further develop the domains. Baselines, guidelines, procedures etc. follow the ISO/IEC 17799:2005 structure and proved information on the different "how to"s. The Access Control domain would contain a baseline for minimum requirements of a 3rd party connection, and quite possibly guidelines to establish and manage such connection. The "Physical and Environmental Security" would provide minimum requirements on equipment security, or for example guidelines on securing offices.
Summary
The policy/standard framework discussed above is based on the ISO/IEC 17799:2005 standard's structure. Other standards (i.e. the ISO/IEC 13335 (1-5):2003) and other directives (i.e. the NIST SP-800 series) are also considered and were used as guidelines in the development process. As a result it provides a coherent framework from information security governance through management to operations.
Since the core elements of this framework are the policy and standard statements, every effort was made to make them as clear and precise as possible. However they have to be considered in the spirit of the law compared to the letter of the law.